What will become of our decentralized networks when quantum computers can break our most secure cryptographic defenses today? If quantum attacks eat away at digital security, then the security of blockchain systems has never been more crucial. Welcome to the Post Quantum Blockchain universe, an incoming paradigm shift strategy combining the blockchain’s resilience and the post-quantum cryptography’s next-generation security to protect the immortal digital universe.
In this article, we discuss the important part that quantum-resistant blockchain will have to play in protecting decentralized networks from the increasing menace of quantum computing.
Understanding Post-Quantum Blockchain
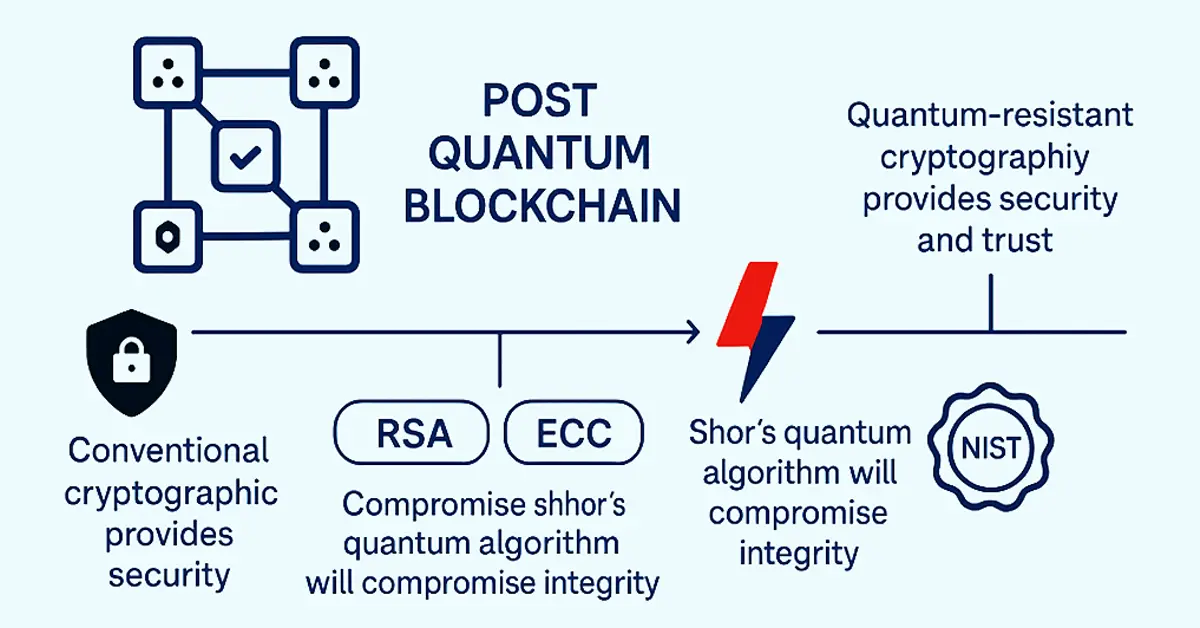
Post Quantum Blockchain is a blockchain network that is protected by highly advanced, quantum computer-immune cryptographically secured algorithms. RSA or ECC are conventional tools used for encryption, which would become sitting ducks against attacks from quantum algorithms like Shor’s, which will compromise their integrity. It poses a humongous risk to decentralized networks operating on such algorithms for data assurance, identity authentication, and secured transactions.
With the integration of quantum-resistant cryptography, these blockchain platforms can provide security and trust in a quantum computer-based future. The National Institute of Standards and Technology (NIST) is attempting to develop ultimate encryption standards to be the new way of doing it, and hence quantum-secure blockchain deployment becomes an unavoidable evolution.
Why Traditional Blockchains Are Vulnerable
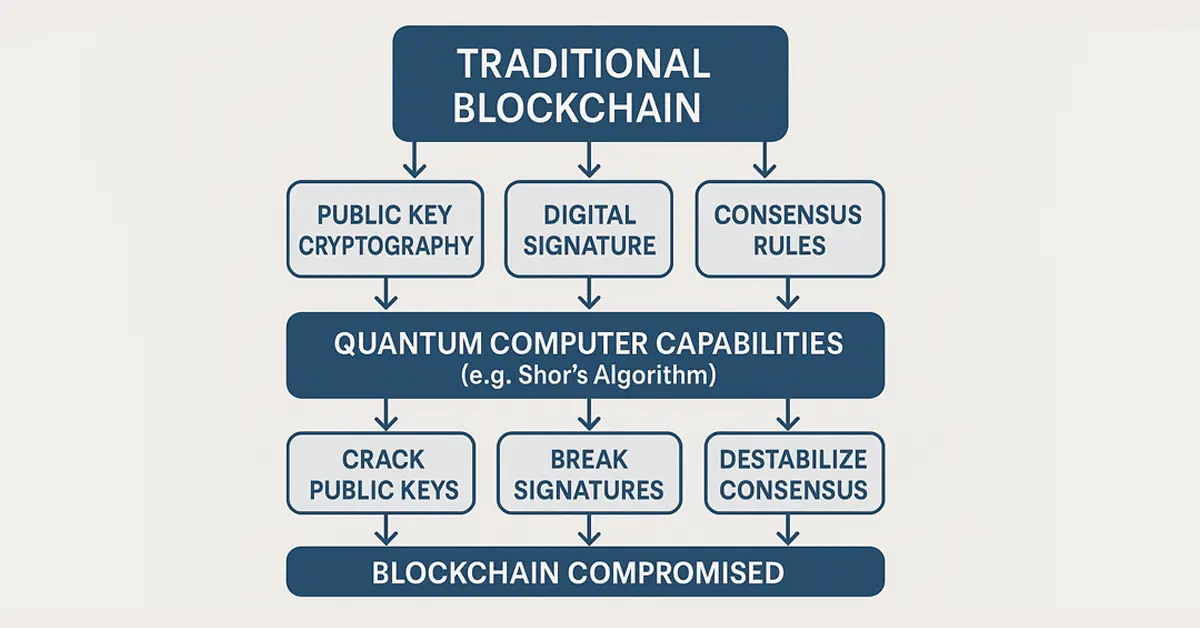
Although blockchain itself is generally considered secure and unalterable, it is not resistant to the increasing threat of quantum computing. Classical blockchains are highly dependent on classical cryptographic methods — namely, public-key cryptography — to protect digital identities, authenticate transactions, and establish consensus among distributed nodes. But with the accelerated advancement of quantum technology, these methods are in serious jeopardy. A sufficiently powerful quantum computer would be able to take advantage of loopholes in such cryptographic schemes to reverse-engineer private keys from public keys, allowing hackers to impersonate the real users. This can result in unauthorized transactions, loss of funds, or even bulk tampering with the blockchain ledger.
Furthermore, quantum computations like Shor’s algorithm can even break the digital signatures that are employed to secure transactions. If such signatures are compromised, they would no longer provide trust in the authenticity or source of a message. Quantum systems would also destabilize consensus systems, which are critical to all participants in a network adhering to a specified state of the blockchain. These findings point to how unprepared systems are at present for a quantum world.
In order to combat these future threats, cryptographers and developers are turning to Post Quantum Blockchain solutions that build on quantum-resistant protocols and algorithms. This next-generation solution can potentially restore trust and security in decentralized systems in the quantum era.
Core Principles Behind Post-Quantum Blockchain
To create a post-quantum blockchain that is resilient, some principles are used-
- Lattice-based cryptography: Lattice-based cryptography is a bedrock, since it is quantum proof. Its mathematical complexity is high and it’s computationally not possible even for quantum computers to reverse-engineer encrypted data, thus it’s a very secure way of safeguarding identity and key exchange.
- Hash-based signatures: Hash-based signatures constitute another central element. They provide secure short-term digital authentication to maintain messages and transactions tamper-evident. Hash-based signatures work with irrevocable one-way functions for a quantum system, as opposed to classical digital signatures.
- Code-based cryptography: Code-based cryptography is also used to ensure a good level of long-term message security. It uses codes that will resist such forms of decryption, whether classical or quantum.
- Zero-knowledge proofs: Finally, we have zero-knowledge proofs, which are incorporated to complete the system. Zero-knowledge proofs allow a party to verify possession of knowledge about a condition or value without sharing underlying information. This maintains confidentiality and guarantees immunity from quantum attacks, such that data confidentiality and trust are achieved in decentralized applications.
Advantages of Post-Quantum Blockchain
1. Future-Proof Security
Most readily apparent benefit of Post Quantum Blockchain is that it will resist quantum attacks. Avoiding future attacks ahead of time, the developers will not need to invest the exorbitant expense of redoing systems down the road.
2. More Privacy
New cryptographic building blocks employed by Post Quantum Blockchain can also enhance the protection of privacy through improved anonymization techniques.
3. Compliance with Regulations
As government agencies start to issue post-quantum compliance requirements, employing Quantum Blockchain protocols puts businesses ahead of the law.
4. Long-Term Data Integrity
In contrast to legacy systems that can grow obsolete in the quantum age, Post Quantum Blockchain solutions guarantee your data is immutable and trusted for decades to come.
Real-World Use Cases for Post-Quantum Blockchain
Some industries are starting to consider Post Quantum Blockchain-
- Finance: The banking industry, for example, is among the first to embrace. Encryption is a major source of security for online transactions, customer identity, and online balances for banks. With the danger of traditional cryptography from quantum computers, quantum-resistant blockchain guarantees long-term security for banking services, cryptocurrencies, and smart contracts.
- Healthcare: Healthcare, where the confidentiality and integrity of patient data are paramount, sees this technology providing tamper-evident storage and transport of sensitive information. Decentralization, and with it the use of quantum-safe encryption, makes for safe sharing of medical records between health providers and shields against leaks and unauthorized alteration.
- Supply Chain: The supply chain sector is also discovering the utility of this new solution. Through the utilization of quantum-resistant blockchain, businesses can create open, immutable records of product origin, transport, and handling. It assists in the prevention of fraud, lowers counterfeiting, and increases efficiency in international logistics.
- Government: Governments are exploring their use for secure administration of digital identity, citizenship authentication, and even voting. With election security and identity fraud issues on the rise, a tamper-proof, quantum-secure blockchain can provide more public trust and operational integrity to democratic and administrative systems.
The Rise of Post Quantum Secured Blockchain
Post quantum secured blockchain technology is a giant leap towards the security of decentralized platforms against the impending threat of quantum computers. Traditional blockchains, though secure against classical attacks, are becoming increasingly susceptible to quantum algorithms that support breaking standard encryption schemes employed.
Conversely, post quantum secured blockchain networks are inherently constructed with quantum resistance. Every single aspect — identity verification, transaction verification, smart contracts, and consensus algorithms — is supported by cryptographic algorithms particularly selected for their quantum decrypt resistance.
This method guarantees that important activities such as signing a contract, digital signing, and multi-party cooperation on data are secure, transparent, and tamper-evident even in the future when all have quantum processors. With a trend of industries going quantum-readiness, implementing such infrastructure is not an upgrade — it is a required building block.
METHODOLOGY: Ensuring AI Safety Through Post Quantum Blockchain
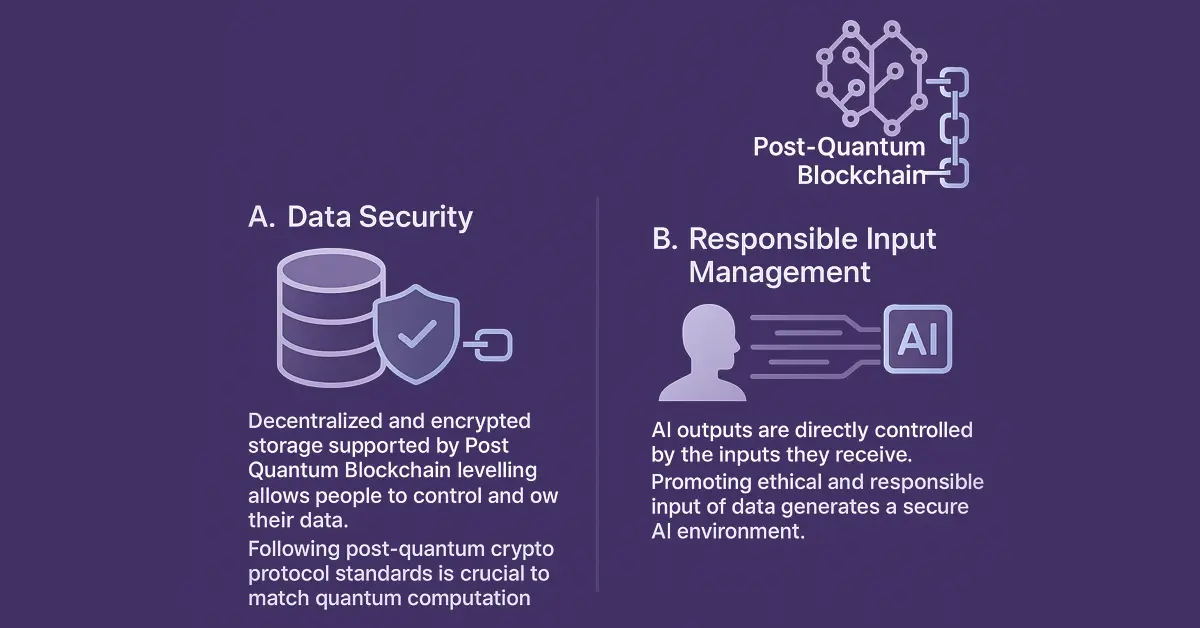
To truly safeguard AI’s influence on society, data integrity must be prioritized above all. As artificial intelligence systems become more intertwined with human decision-making, preventing malicious replication of identity and the misuse of personal data is crucial. One reliable approach is the integration of Post Quantum Blockchain…
Comments
Post a Comment