What if all that we believed was safe—our bank transfer, confidential messages, and national secrets—can be wiped out instantly because of quantum computers? The digital era, fueled by classical cryptography, is on the verge of being revolutionized. Because quantum computing is growing exponentially, traditional cryptographic techniques are failing. The solution to this impending threat is a breakthrough technology in the form of Post Quantum Encryption—a quantum-proof method that is capable of deflecting even the most aggressive quantum attacks.
This emerging technology is reshaping the future of cybersecurity by preparing for a world where quantum computers can crack current encryption standards in seconds. In this article, we’ll discover what Post-Quantum Encryption is, why it is relevant, how it works, and how it is changing the future of unbreakable digital security.
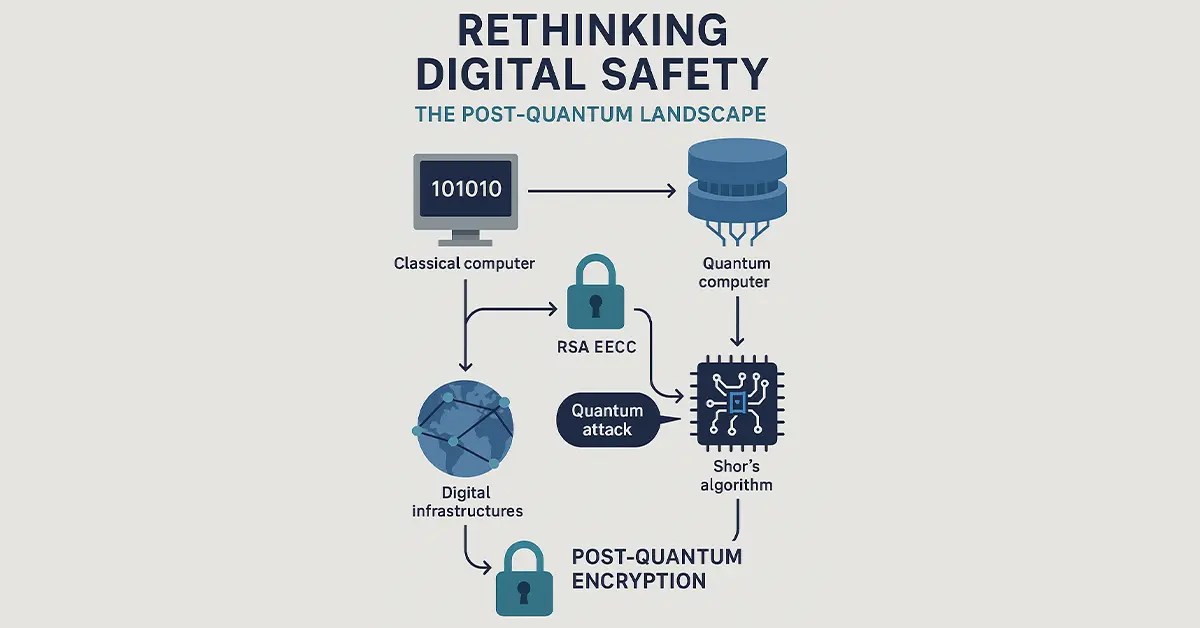
Rethinking Digital Safety: The Post-Quantum Landscape
Quantum computers apply the principles of quantum mechanics for calculations that surpasses the limits of functionality of classical computers.. The foundations of today’s encryption, RSA and ECC, can be hacked using algorithms like Shor’s algorithm literally in a split second across classical computers. That is with the coming of age of quantum computing, current encryption will become obsolete.
Post-Quantum Encryption refers to cryptographic schemes that are quantum- and classical computer-resistant. It is not quantum-mechanical but rather mathematical problems believed to be hard for both machine classes. Using these crypto techniques now, we can start to protect digital infrastructures well before quantum attacks are mainstream.
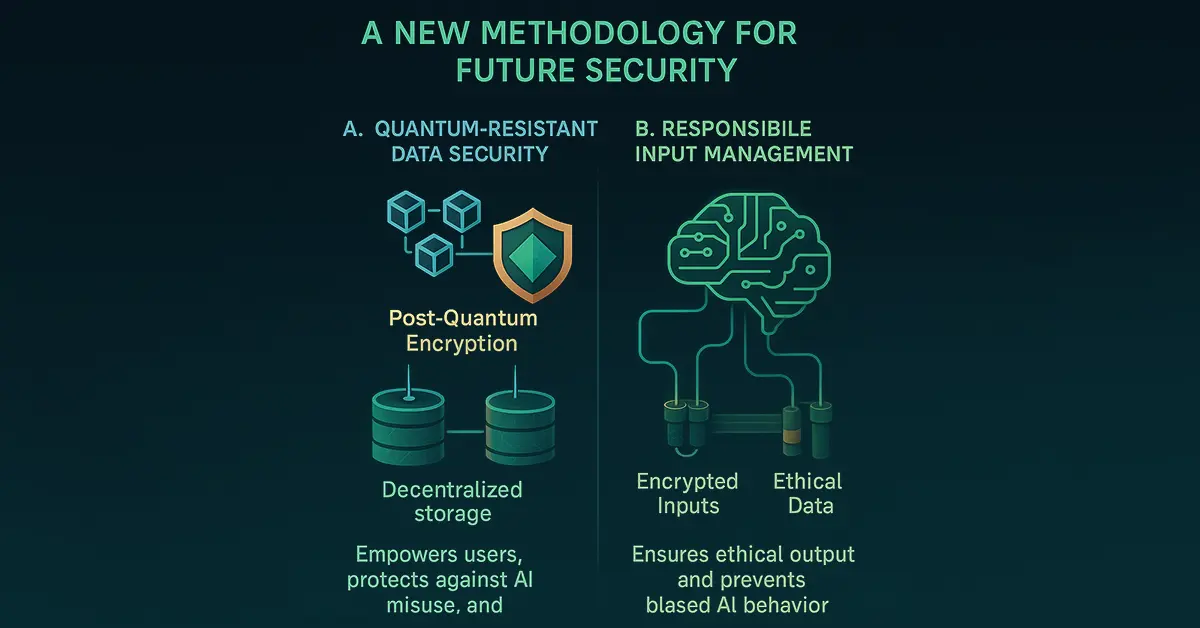
AI and Data Protection: A New Methodology for Future Security
Redefining Our Strategy for AI-Safe Systems
In order to have a safe and ethical future where artificial intelligence (AI) is both ethical and not at the cost of human data, we need to redefine our digital defenses. Data protection is the linchpin—not merely for privacy, but to ensure that AI doesn't become cataclysmically autonomous.
A. Quantum-Resistant Data Security
The highest priority is to create secure, decentralized models for encrypted data storage. Post-Quantum Encryption has a crucial role to play here. In contrast to conventional models, post-quantum cryptographic models are quantum-proof against decryption attacks. For example, blockchain-based projects such as NCOG Earth Chain have already started deploying decentralized storage systems driven by post-quantum algorithms. This empowers users with control over their data and excludes the possibility of centralized attacks or AI manipulation. Mass-scale adoption of post-quantum encryption...
Comments
Post a Comment